-
Integrating User-Centric Design in IT Projects: A Comprehensive Guide
User-centric design, a philosophy at the heart of modern software development and information technology (IT) projects, places the end user at the forefront of the design process. This approach involves…
-
A Comprehensive Exploration of Protecting Your Digital Presence
With smartphones and tablets becoming indispensable companions in our daily lives. From communication and banking to entertainment and productivity, these devices have revolutionized how we interact with the world. However,…
-
A Comprehensive Dive into the World of Digital Forensics
Digital forensics is a beacon of truth, unraveling the mysteries of cyber incidents and breaches. This comprehensive exploration delves into the intricate world of digital forensics, uncovering ten pivotal aspects…
-
Safeguarding the Digital Horizon: Navigating Cloud Security Challenges
Cloud computing has emerged as a game-changer, empowering organizations to scale, innovate, and optimize operations. However, this cloud migration brings a pressing concern: security. As organizations entrust their sensitive data…
-
Unveiling the Enigma Within: Navigating the Realm of Insider Threat Management
The vulnerability posed by insider threats is a prominent concern that demands a comprehensive and vigilant approach. This detailed exploration delves deep into the intricate domain of insider threat management,…
-
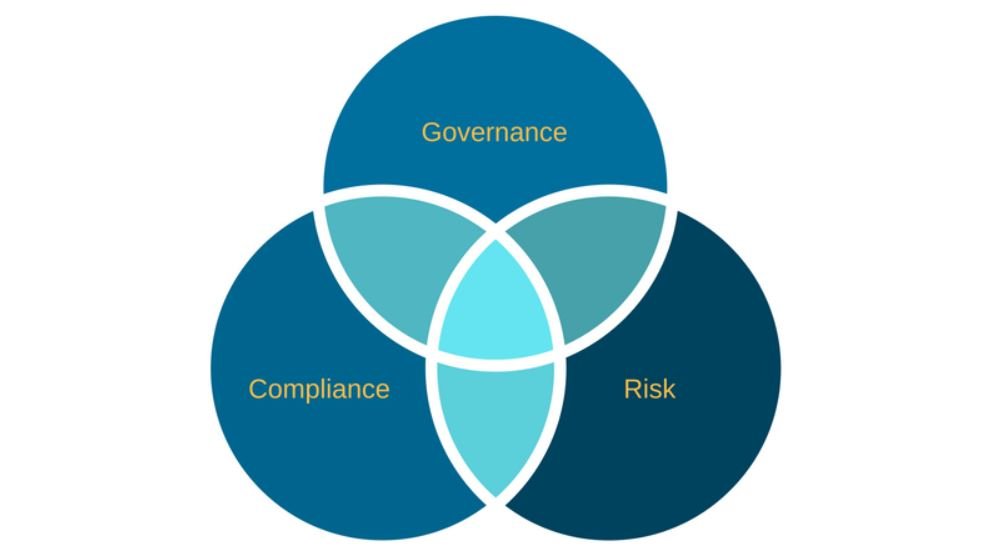
Ethical Navigators: Unraveling the Governance, Risk, and Compliance Odyssey
In a world of data breaches and regulatory complexities, the triumvirate of Governance, Risk, and Compliance (GRC) is the sentinel of order and protection. This extensive exploration unveils the multifaceted…
-
Decrypting Defenses: A Comprehensive Insight into Ethical Hacking and Penetration Testing
Ethical hacking and penetration testing are critical allies in this ongoing skirmish, allowing organizations to identify weak points before malicious actors can exploit them. This comprehensive exploration delves into the…
-
Navigating Web Application Security: A Deep Dive into 10 Crucial Defense Strategies
Web applications are the conduits through which organizations interact with users and conduct business. However, the digital landscape is rife with threats that can compromise these vital gateways. This comprehensive…
-
Comprehensive Guide to Network Security: Top 10 Aspects Explained
Network security has emerged as the bedrock of cyber defenses in the digital age, where data flows seamlessly across the virtual landscape. Regardless of size, organizations rely on robust network…
Search
Recent Posts
- Vulnerability in Dell RecoverPoint for Virtual Machines could allow arbitrary code execution
- Multiple vulnerabilities in Ivanti Endpoint Manager Mobile could allow remote code execution
- A vulnerability in the WatchGuard Fireware operating system could allow arbitrary code execution.
- Vulnerability in Cisco AsyncOS Could Allow Remote Code Execution